Sprocket Attack Surface Management Tool
Sprocket's no-cost ASM tool automatically uncovers all your exposed assets giving you full visibility of your environment from an attacker's point of view.
Create Account



Why Choose Sprocket ASM?

-
Tool built by Penetration Testers - developed by experts who know how attackers think and what they target
-
Zero-cost entry - start protecting your organization without any cost barrier
-
Seamless integration with CPT - easily transition to continuous penetration testing for deeper insights and active threat validation.
-
First step to CTEM - scoping part of it, critical to do to get to CTEM - validation and mobilization

WATCH ASM TOOL DEMO
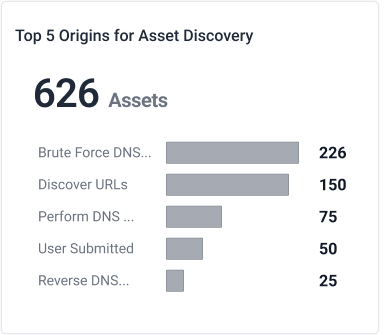
Comprehensive Tool for Attack Surface Visibility
- Discover all your exposed assets — domains, IP addresses, services, and much more — automatically.
- Cut through the noise and focus on what matters most with clear, actionable risk priorities.
- Gain control of your security posture with proactive asset discovery and effective management
Tackling Scoping, Discovery and Prioritization
Our focus on CTEM
According to Gartner®, “The importance of a CTEM program, when compared to previous functions, such as vulnerability management (VM), is that it considers the “why” and “how” elements of what is discovered. Importantly, the scoping exercise, before a discovery exercise, is designed to keep the focus on what is important to the business. CTEM is not a purely risk-driven exercise either. Transforming a traditionally diagnostic function into an actionable set of outcomes requires clarity regarding objectives.”
We believe Sprocket ASM ensures that accurate scoping, grounded in business risk and potential impact, takes precedence over merely counting discovered assets and vulnerabilities.
By focusing on what truly matters, we help organizations prioritize their efforts for maximum security and operational value.
“More developed vulnerability management projects generally include good initial scoping for internal, on-premises and owned assets. A CTEM program goes beyond self-inflicted vulnerabilities and also takes the “attacker’s view,” beyond the traditional common vulnerabilities and exposures “(CVEs)” (see also Using Security Testing to Grow and Evolve Your Security Operations). When trying to find the right scoping for a CTEM program pilot, good candidates include:
-
External attack surface — It combines a relatively narrow scope (for most organizations) and a growing ecosystem of tools.
- SaaS security posture — While tool maturity is still lacking, increasing remote workforce led to more critical business data hosted on SaaS, ensuring easier communication about the risks.”
Gartner®, Implement a Continuous Threat Exposure Management (CTEM) Program, By Jeremy D'Hoinne, Pete Shoard, Mitchell Schneider, 11 October 2023. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.