Browse Classifications
- All Resources
- Strategic Content
- Technical Content
- Ahead of the Breach Podcast Content
- Partner Program Content

Setup OpenVPN for fast and secure deployment of your dropbox infrastructure.
In part 1 I covered different options to look for when choosing a pentest dropbox. In this part I'll walk you through my OpenVPN setup for connectivity and management of dropboxes. Part 3 walks through the provisioning of a dropbox to work with this setup.
This method is superior to SSH since OpenVPN is designed for this type of remote connectivity.
This setup will save you a lot of time during your internal pentests. This reason alone is worth using openVPN. If you spend a little time up front building simple infrastructure, you'll be rewarded with more time to test and less time managing connectivity. Here are some other reasons:
If these reasons are not convincing enough, I'd like to hear your feedback.
OpenVPN is our critical infrastructure. Here is a visual of what we are building:
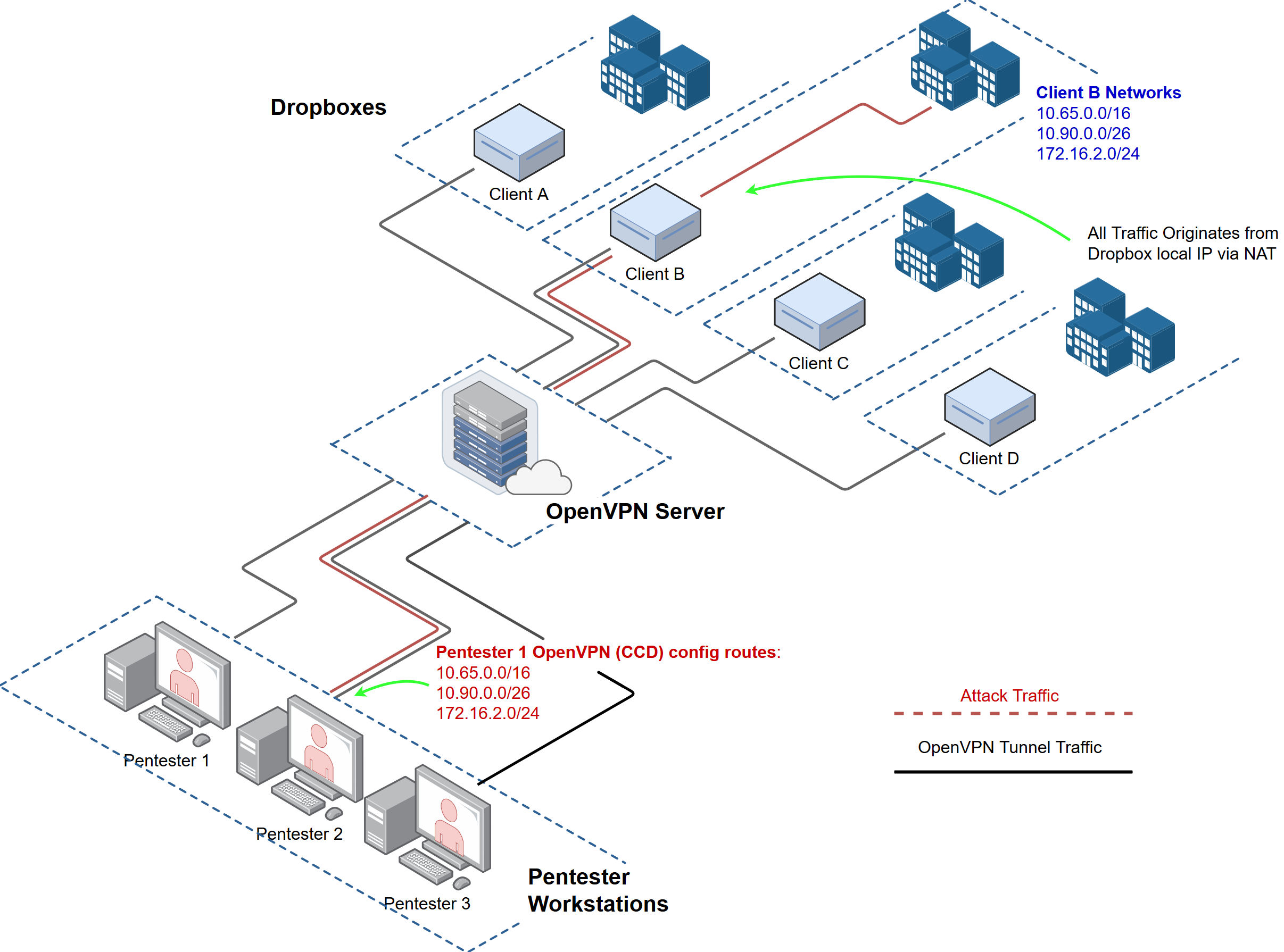
The light blue boxes labeled "ClientX" are the physical dropboxes. The openVPN server can be hosted on perm or in the cloud.
Starting from a fresh Ubuntu server install, we'll setup OpenVPN:
apt update
apt -y upgrade
apt install openvpn easy-rsacd into /etc/openvpn
Create a file /etc/openvpn/pttunnel.conf with the following data:
dev tun0
tls-server
user nobody
group nogroup
# Openvpn tunnel network
server 10.254.254.0 255.255.255.0
# IP Address we listen on
local <LOCAL_IP_OF_SERVER>
# Port and Protocol
port 1194
proto tcp
comp-lzo
cipher AES-256-CBC
# IPP allows you to statically assign tunnel network IPs to dropboxes
#ifconfig-pool-persist /etc/sysconfig/openvpn/ruvpn-ip-pool.txt
# mgmt & log settings
management 127.0.0.1 1196
log /var/log/openvpn
mute-replay-warnings
# verbose level, turn up if troubleshooting for more logs. 6 is usually good.
verb 3
# Maximum number of simultaneous clients
# enabling this allows multiple connections using the same cert. However, this is insecure.
# if someone steals your certs from a dropbox both the legit and malicious connections could exist simultaneously.
#max-clients 50
client-to-client
client-config-dir ccd
#Option, set renegotiation time
#reneg-sec 86400
#location of cert files
dh /etc/openvpn/easy-rsa/keys/dh2048.pem
cert /etc/openvpn/easy-rsa/keys/pttunnel.crt
ca /etc/openvpn/easy-rsa/keys/ca.crt
key /etc/openvpn/easy-rsa/keys/pttunnel.key
# set this up upon first revoke
#crl-verify /etc/openvpn/easy-rsa/keys/crl.pem
#Timeout for restarting the tunnel on client end if it loses connection
keepalive 10 60
persist-tun
persist-key
#keep mtus low to account for additional encapsulation
link-mtu 1250
mssfix 1250
Create the client configuration directory (aka ccd): mkdir /etc/openvpn/ccd
Easy-rsa is a set of scripts to make certificate management painless. Copy over the easy-rsa directory:
cp -a /usr/share/easy-rsa /etc/openvpn/cd into /etc/openvpn/easy-rsa and generate a server certificate using the following commands:
. vars
./clean-all
./build-ca
./build-dh
./build-key-server pttunnel
touch keys/crl.pemTip: you can improve your security by keeping your certificate authority on an internal system/fileshare/git repo, etc.
At this point you should be able to run the OpenVPN server.
/etc/openvpnsudo openvpn -config pttunnel.confFor the lucky people not using systemd ;-)
update-rc.d openvpn enable
Start openVPN now as a daemon:
sudo /etc/init.d/openvpn start
cd into /etc/openvpn/easy-rsa and generate a certificate using the following commands:
Replace 'pentester01' below with the names of each pentester
. vars
./build-key pentester01You should only have to do this once for each pentester/consultant. At Sprocket sometimes a pentester may have multiple workstations they connect from. In that case, we generate separate certificates for each of their machines (ex: pentester01, pentester01-windows).
In this example I'm assuming the pentester/consultant is using Ubuntu Desktop, but Windows or OSX will work.
Securely copy the following certificates you generated in the previous section (from the OpenVPN server):
/etc/openvpn/easy-rsa/keys/ca.crt/etc/openvpn/easy-rsa/keys/pentester01.crt/etc/openvpn/easy-rsa/keys/pentester01.key ...and copy them to the /etc/openvpn directory on the workstation.
Create the OpenVPN client configuration file /etc/openvpn/pttunnel-client.conf with the following data:
client
dev tun
proto tcp
remote-cert-tls server
remote <PUB_IP_OF_OPENVPN_SRV> 443
remote <PUB_IP_OF_OPENVPN_SRV> 80
remote <PUB_IP_OF_OPENVPN_SRV> 53
persist-key
persist-tun
verb 3
ca <FULL_PATH_TO_CA.crt>
cert <FULL_PATH_TO_PENTESTER01.crt>
key <FULL_PATH_TO_PENTESTER01.key>
cipher AES-256-CBC
comp-lzoAfter copying the certificates from the previous section onto the pentester's workstation. Test the OpenVPN configuration file and verify the tunnel establishes:
/etc/openvpnopenvpn -config pttunnel-client.conf verb directive on the client to better understand the failure.remote directive to point to the internal IP address of the OpenVPN server for testing.route -n
tcpdump -nni tun0
nc 127.0.0.1 1196 <type: 'status' in shell> Congrats! You should now have a working OpenVPN server that pentesters can connect to. However, its not very useful until we get our dropboxes connected.
Continue to part 3 to learn how to provision a dropbox to work with this OpenVPN server.
Continuous Human & Automated Security
Continuously monitor your attack surface with advanced change detection. Upon change, testers and systems perform security testing. You are alerted and assisted in remediation efforts all contained in a single security application, the Sprocket Platform.