
Pro tips for purchasing and aging phishing domains
This is a must now if you plan to evade phishing technical controls.
Good command-and-control infrastructure requires a known, trusted domain. When you’re first starting out, this can be difficult to find, but luckily other testers have provided many great resources.
So, let’s dive into what’s available and how to make the right choices when building out an attack infrastructure.
ID and purchase the best domains
First things first: purchase a domain. In this process, you’ll most likely consider either of the following options:
-
Purchasing a domain similar to your target's apex domain
-
Purchasing a domain with an existing and strong reputation
If you’re looking for a domain similar to your target domain, check out the link below:
dnstwister
The anti-phishing domain name search engine, based on dnstwist.
 https://dnstwister.report
https://dnstwister.report
Search your target apex domain and this site will help you find similar ones for sale. For example, I performed a search for our company domain:

Additionally, good place to look for reputable domains to purchase is linked below:
Expired Domains | Daily Updated Domain Lists for 472 TLDs
You can currently find the following domains in the database. The lists get updated regularly and new domains get added to the database.
 https://www.expireddomains.net
https://www.expireddomains.net
This place is the cream of the crop when it comes to looking for reputable domain names. I’d recommend creating an account so you can browse and save your finds. To uncover the good stuff, go to deleted domains:

Select the filter option:

Try out my go-to filter settings:

You can also tab over and choose from a set of desired TLD's and SEO categorizations. Don’t worry too much about domain categorization; we can consider that at a later point. For now, click "Apply Filter" and you’re on your way.
Each column header is related to something different. I like to find a domain with a large number of backlinks from other domains. This means the domain has been around and used – therefore, the chances of this domain being marked as malicious are pretty low.
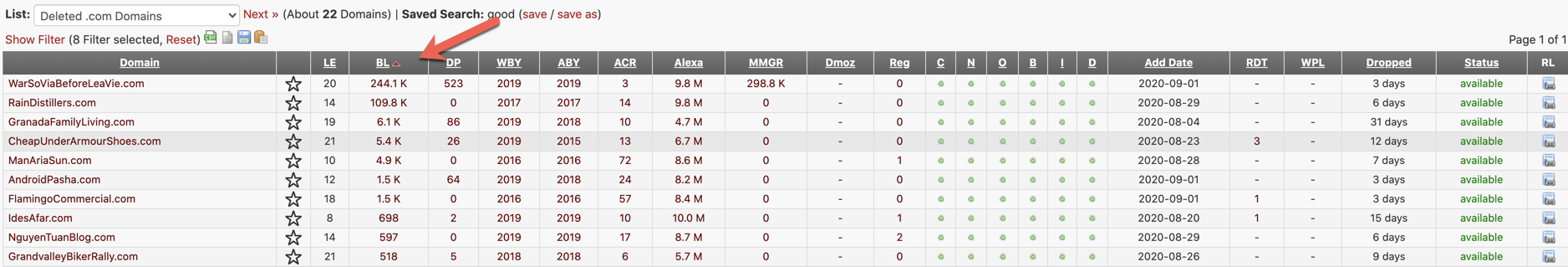
Some other indicators I look for when buying domains:
-
Length. Look to pick fairly short domains. The longer the domain, the more it stands out to defenders.
-
Lifetime. Pick domains that have been around for a bit. This is indicated by the ABY and WBY column headers.
-
Association. A high number of [archive.org] crawl results also indicate that the domain is associated with known sites. You can actually go back and grab the page content to rehost the original site while aging the domain.
After you have selected some domains, you need to take a few steps before finalizing a purchase. I recently made the mistake of purchasing a domain that met the above criteria but ended up being permanently categorized by security solutions as unsavory.
To prevent something similar from happening to you, grab your domain and head to the following sites to perform a search:
Internet Archive: Digital Library of Free & Borrowable Books, Movies, Music & Wayback Machine
Internet Archive is a non-profit digital library offering free universal access to books, movies & music, as well as 468 billion archived web pages.
 https://archive.org
https://archive.org
Make sure your domain was never registered in association with malicious content or unsavory websites.
How to age a domain
After you purchase a domain, you need to build its reputation. This may be difficult depending on how long the domain has previously been in use. This is why it’s important to buy your domains far in advance and effectively keep track of what you have.
So, let's say you bought [acme.com]. Some key next steps would be:
-
Setup reliable DNS records.
-
Setup fake sites associated with your domain.
-
Link your domain to a trusted mail server.
-
You can even send out some benign mail with it.
If you specifically want to use this domain for phishing, do the following:
-
Set up your mail records as soon as possible.
-
Don't do anything goofy.
-
ALWAYS have proper mail records set up, including having proper DKIM and SPF record provisions.
For hosting sites and your payloads:
-
Set up your records early.
-
Get a certificate associated with it.
-
Host a site with valid content and do so early in the process.
-
Point it at some known records similar to your site's categorization.
Wrapping Up
In a future article, I’ll outline the process for cloning sites and warming up infrastructure. Some great tools are out there to help with this process. And, we may even take a look at automation to make our lives easier.
For now, remember these key takeaways:
-
Buy your domains ahead of time.
-
Age your infrastructure to build trust.
You can never spend too much time on this. Good infrastructure will make or break an engagement.
Continuous Human & Automated Security
The Expert-Driven Offensive
Security Platform
Continuously monitor your attack surface with advanced change detection. Upon change, testers and systems perform security testing. You are alerted and assisted in remediation efforts all contained in a single security application, the Sprocket Platform.
Expert-Driven Offensive Security Platform
- Attack Surface Management
- Continuous Penetration Testing
- Adversary Simulations


